The cybersecurity landscape is evolving at a breakneck pace, and understanding the interplay between ransomware operations, threat actors, and campaign evolution has never been more critical. Today, we are excited to highlight the latest update to one of the most comprehensive open-source threat intelligence resources available: the Ransomware Ecosystem Map by the Orange Cyberdefense CERT – World Watch team.
View on GitHub
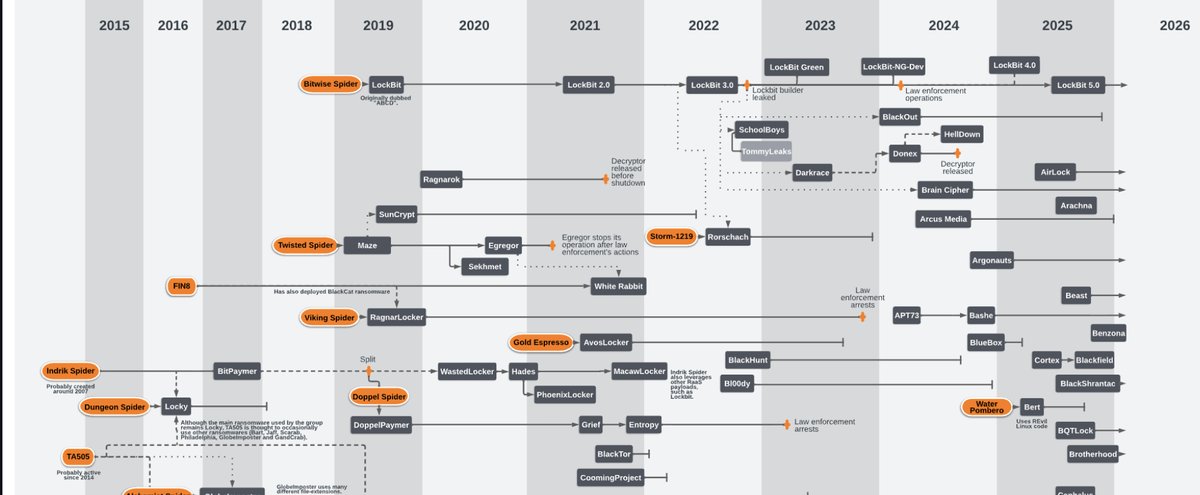
What Is the Ransomware Ecosystem Map?
The Ransomware Ecosystem Map is a visual and analytical representation of ransomware groups, their variants, and the complex relationships and timelines connecting them. Hosted on GitHub, this project tracks over 300 ransomware families and associated actors from 2015 through 2026, helping defenders, analysts, and researchers make sense of a sprawling and sometimes opaque threat landscape.
Rather than attempting to list every existing group, the map focuses on meaningful associations and trends, emphasizing relevance and observed activity over exhaustive enumeration. The team curates entries based on internal research, incident response data, and corroborated external reports, acknowledging that exact attribution in cybercrime remains complex and fluid.
What’s New in Version 29 (January 2026)
The January 2026 release—Version 29—brings a host of improvements and additions, reflecting the latest developments in ransomware operations:
Updated Relationships and Edits
Several previously catalogued ransomware actors and variants have been edited to reflect updated intelligence and refined connections within the ecosystem. These include widely observed families and aliases such as:
- Apos
- BlackSuit
- Cactus
- Dharma
- Embargo
- Hellokitty
- LukaLocker
- Nitrogen
- Phobos
- Radar
- Ransomed
- Thanos
These edits improve the accuracy and context of historical and ongoing activity.
New Additions
Version 29 introduces an extensive list of new ransomware groups and threat actor labels, many of which emerged or gained prominence between 2024 and 2025. Notable new entries include:
- Ailock (June 2025)
- Aware (January 2026)
- Beast (July 2025)
- BlackField (October 2025)
- Coinbase Cartel (September 2025)
- DarkLulz (June 2025)
- Dire Wolf (May 2025)
- Kraken (February 2025)
- Lockbit 5.0 (September 2025)
- VECT (January 2026)
…and many others representing a broad spectrum of actors and code families. This expansion underscores the dynamism of ransomware activity and the importance of ongoing tracking for defensive and research purposes.
Why This Map Matters
Ransomware remains one of the foremost cyber threats facing organizations globally, impacting sectors from healthcare to critical infrastructure. By centralizing threat actor relationships, aliases, and timelines in a single resource, the Ransomware Ecosystem Map helps:
- Security teams understand lineage and evolution of threats
- Threat intelligence analysts contextualize attacker behavior
- Researchers correlate public reporting with observed trends
- Incident response practitioners anticipate actor tactics and overlap
How to Access the Map
The Ransomware Ecosystem Map is freely available on GitHub as a PDF and is updated regularly by the Orange Cyberdefense World Watch team. The project is maintained under an open-source model and welcomes community feedback and issue reporting for continuous improvement.

Comments
Submit comment
No comments yet. Be the first to share your thoughts!