This year marked a turning point in the cybercrime ecosystem. While established players like LockBit and Clop continued their campaigns, the real story of 2025 was the emergence of new ransomware groups that quickly made their presence felt. These actors introduced fresh tactics, leveraged advanced encryption schemes, and embraced multi-layered extortion strategies, proving that ransomware remains one of the most disruptive threats in cybersecurity.
The Rise of New Threat Actors
According to data from ransomware.live, dozens of new groups appeared in 2025, many of them launching aggressive campaigns within weeks of surfacing. Unlike previous years, these groups demonstrated a high degree of specialization—targeting critical infrastructure, healthcare, and financial services with precision.
Our analysis focused on groups whose official creation date was after January 1, 2025, based on the date field in the ransomware.live dataset. We then correlated this with victim disclosures from the same source to understand their impact.
Top 10 New Groups by Victim Count
Here are the most active newcomers of 2025:
1. Sinobi — 187 victims
2. Babuk2 — 169 victims
3. Devman — 155 victims
4. Worldleaks — 112 victims
5. Lockbit5 — 108 victims
6. Nightspire — 102 victims
7. Nova — 82 victims
8. Thegentlemen — 80 victims
9. Warlock — 78 victims
10. Coinbasecartel — 59 victims
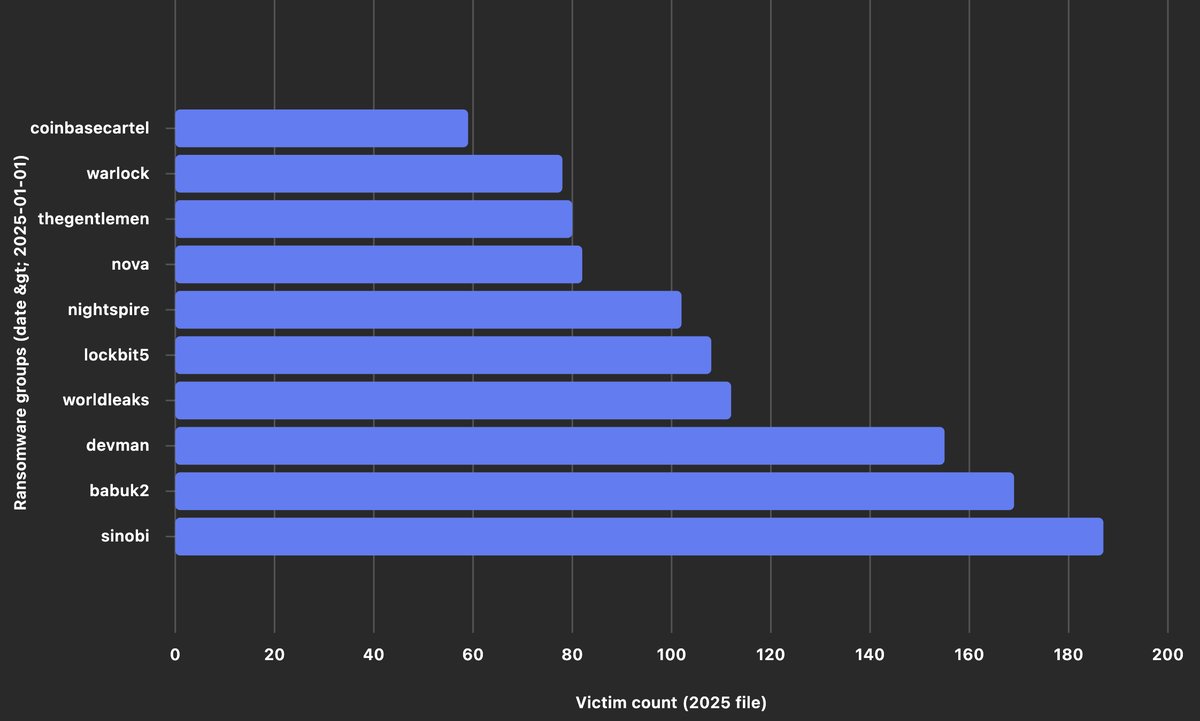
These numbers highlight how quickly new actors can scale their operations. Groups like Sinobi and Babuk2 not only appeared late in the year but still managed to compromise hundreds of organizations globally.
What Makes These Groups Different?
* Rapid Deployment: Many of these groups launched campaigns within days of being detected.
* Innovative Techniques: Use of double and triple extortion, data auctions, and advanced obfuscation.
* Target Diversity: From SMBs to large enterprises, no sector was immune.
Looking Ahead
The emergence of these groups underscores a critical reality: ransomware is not going away. In fact, it’s becoming more fragmented and harder to track. Organizations must adopt proactive defense strategies, including:
* Continuous monitoring for indicators of compromise.
* Regular backups and tested recovery plans.
* Employee awareness and phishing resistance training.
Source: Ransomware.live


Comments